SSL EV Code Signing Certificates: Why Hardware Devices Are Now Required and How to Streamline the Process

In today’s software security landscape, SSL EV Code Signing certificates are vital for ensuring the authenticity and integrity of software files like DLLs, installers and executables.
These certificates guarantee that your distributed software is trustworthy and untampered.
However, recent changes by the Certificate Authority/Browser (CA/B) Forum now mandate that code signing certificate keys be stored on a hardware security module (HSM) or a token that meets strict security standards such as FIPS 140-2 Level 2 or Common Criteria EAL 4+.
While these new requirements bolster security, they also bring about delays, increased complexity and higher costs for developers and organizations.

Why Are EV Code Signing Certificates Now Issued Through Secure Hardware Devices?
The adoption of hardware devices for EV Code Signing Certificates responds to the demand for enhanced cybersecurity measures and compliance with industry standards. Key reasons include:
- Enhanced Security Against Cyber Threats: Storing the private key on a hardware device like a USB token or Hardware Security Module (HSM) ensures it stays offline, reducing exposure to malware and advanced cyberattacks.
- Compliance with FIPS Standards: Organizations managing sensitive data, such as government contractors, must adhere to FIPS 140-2 compliance, which mandates secure storage and encryption of cryptographic keys.
- Certification Authority (CA) Policies: Leading CAs like DigiCert and GlobalSign now require hardware-based key storage to ensure only authorized access to EV Code Signing Certificates, minimizing risks of misuse or fraud.
- Regulatory Compliance for Secure Software Development: Stricter regulations from cybersecurity frameworks demand robust measures, including the mandatory use of hardware devices for code signing certificate issuance to mitigate security breaches.

Practical Challenges of Using Hardware Devices: Delays, Complexity, and Costs
While hardware-based EV Code Signing Certificates offer substantial security benefits, implementing them presents several challenges for organizations:
- Increased Operational Complexity: Setting up an HSM or USB token solution requires specialized knowledge, posing difficulties for small businesses without dedicated IT support.
- Delays in Certificate Issuance: The integration of physical devices and additional identity validation steps extends the timeframe for obtaining a certificate. What once took hours now requires days or weeks due to logistics.
- Higher Implementation Costs: Purchasing and maintaining hardware security devices like HSMs or thumb drives incurs significant expenses. Outsourcing to managed certificate services may reduce workload but adds service fees.
By addressing these challenges, organizations can effectively streamline the adoption of hardware-based EV Code Signing Certificates while maintaining robust software security practices.

A Workaround to Simplify the Process
Despite these hurdles, you can streamline obtaining an EV Code Signing certificate by following these steps:
On the other hand, custom software can be built specifically to meet the unique requirements of the company and can be more flexible to evolve along with the company. However, it usually involves a longer implementation time, higher initial cost, and may require more technical expertise to maintain. The company should therefore consider its budget, timeline, in-house technical expertise, and unique business needs, as well as potential future scaling and development, to decide the most appropriate route.
Step 1: Purchase a New EV Code Signing Certificate
- Visit DigiCert’s website to purchase an EV Code Signing certificate.
2. Select the storage option to use a hardware security module (e.g., Azure Keys, AWS Code Signing).
3. Generate a Certificate Signing Request (CSR) if you don’t already have one:
- Use the DigiCert CSR Creator tool.
- Follow these instructions to create a CSR on a Windows machine.
3. Upload the CSR file to complete the purchase.
After submitting your request, DigiCert will validate your business information against public records. Once validated, you will receive a ZIP file containing the CRT file.
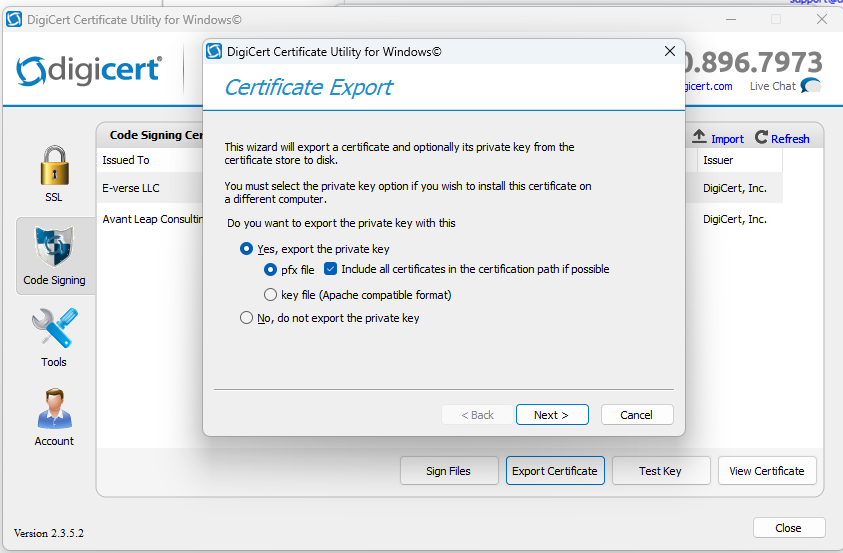
Step 2: Create the PFX File
1. Download the DigiCert Certificate Utility.
2. Open the utility and import the CRT file into the Code Signing section.
3. Export the certificate as a PFX file:
- Set a secure password during the export process.
Step 3: Sign Your Files
Install SignTool on your Windows machine. Use the following command to sign your files:
signtool.exe sign /f "credentials.pfx" /p yourPassword /t http://timestamp.digicert.com "file/to/sign"
Automating the Code Signing Process with GitHub Actions
GitHub Actions is a continuous integration and continuous delivery (CI/CD) platform that allows you to automate workflows directly in your GitHub repository.
With Actions, you can define custom workflows to build, test, and deploy your code automatically in response to events like code pushes or pull requests.
Step-by-Step Guide to Automate Signing with GitHub Actions
Follow these steps to automate the signing process using GitHub Actions:
Step 1: Prepare Your Environment
- Store your PFX file securely in an S3 bucket or similar service.
- Add the following secrets to your GitHub repository:
CERTIFICATE_S3_URL: The URL to download your PFX file.AWS_S3_CERTIFICATE_KEY_ID: API key or credentials for accessing the S3 bucket.CERTIFICATE_KEY: The password for your PFX file.
Step 2: Create a GitHub Actions Workflow
- In your repository, create a new directory
.github/workflowsif it doesn’t already exist. - Add a new YAML file, e.g.,
sign-code.yml.
Step 3: Download the PFX File
Add the following steps to your YAML file to securely download the PFX file:
- name: Get certificate
run: |
$url = "${{ secrets.CERTIFICATE_S3_URL }}"
$outputFilePath = "$GITHUB_WORKSPACE/credentials.pfx"
$apiKey = "${{ secrets.AWS_S3_CERTIFICATE_KEY_ID }}"
$headers = @{ "x-api-key" = $apiKey }
Invoke-RestMethod -Uri $url -Headers $headers -OutFile $outputFilePath
- name: Define certificate key
run: |
echo "CERTIFICATE_KEY=${{ secrets.CERTIFICATE_KEY }}" | Out-File -FilePath $Env:GITHUB_ENV -Encoding utf8 -Append
shell: pwsh
- name: Define certificate location
run: |
echo "CERTIFICATE_LOCATION=$GITHUB_WORKSPACE/credentials.pfx" | Out-File -FilePath $Env:GITHUB_ENV -Encoding utf8 -Append
shell: pwsh
Step 4: Sign Executable Files
Add the following steps to locate and sign your files:
- name: Sign files
run: |
$files = Get-ChildItem -Path ./location/to/files -Filter "*.exe" -Recurse | ForEach-Object { $_.FullName }
foreach ($file in $files) {
& "C:\Users\runneradmin\.nuget\packages\signtool.0.17763.132\tools\signtool.exe" sign /f ${{ env.CERTIFICATE_LOCATION }} /p ${{ secrets.CERTIFICATE_KEY }} /t http://timestamp.digicert.com "$file"
Write-Host $file
}
shell: pwsh
Step 5: Commit and Push
- Save your
sign-code.ymlfile. - Commit and push the changes to your repository.
GitHub Actions will automatically run the workflow when triggered, signing your executable files with your PFX certificate.
Streamlining Your Workflow with Hardware-Based EV Code Signing Certificates
The shift to hardware devices for EV Code Signing Certificates represents a crucial step toward improving cybersecurity standards and protecting sensitive software from misuse.
While this transition enhances security by safeguarding private keys, it also introduces challenges like increased complexity, longer issuance times, and higher costs.
To navigate these obstacles effectively, organizations can adopt best practices such as automating key steps in the signing process with tools like GitHub Actions.
Additionally, choosing reliable third-party providers or leveraging secure Hardware Security Modules (HSMs) can significantly reduce operational overhead.
By proactively addressing these changes, businesses can maintain seamless workflows while staying compliant with updated Certification Authority (CA) guidelines and regulatory requirements.
Embracing these measures ensures not only adherence to security standards but also streamlined processes, enabling your organization to focus on delivering secure, trusted software to your users.
Valentin Noves
I'm a versatile leader with broad exposure to projects and procedures and an in-depth understanding of technology services/product development. I have a tremendous passion for working in teams driven to provide remarkable software development services that disrupt the status quo. I am a creative problem solver who is equally comfortable rolling up my sleeves or leading teams with a make-it-happen attitude.
